Redefines WAF with Contextual AI-Engine
AI-Driven Next Generation of WAF
MaxiSafe's AI-WAF addresses the challenges by integrating advanced detection techniques that extend beyond conventional rule-based logic and consolidate multiple layers of protection to provide comprehensive security coverage.
- General Protection
- Managed Rules targeting known vulnerabilities, such as SQL injection, XSS, File inclusion, and Webshell detection.
- Behavioural Analysis for identifying brute-force attacks, leeching attempts, and reconnaissance scans.
- Advanced Protection
- Custom Rule Sets tailored to business-specific threats, including credential stuffing, API abuse, and data scraping.
- Progressive Challenging Mechanisms to handle repeat offenders and slow-rate attacks.
- HTTP Compliance Inspection
- Enforces protocol compliance by inspecting request and response structures for anomalies and potential exploits.
- Validates HTTP methods, headers, and content types to prevent header manipulation and unauthorized requests.
- Intelligent Contextualisation
- analyses entire request sequences to understand contextual relationships, identifying malicious intent even when payloads are obfuscated or fragmented.
- Incorporates semantic analysis to detect complex attack patterns embedded in otherwise benign-looking requests.
- Reduces false positives by correlating multiple request attributes (e.g., headers, parameters, payload structure) to form a comprehensive threat profile.
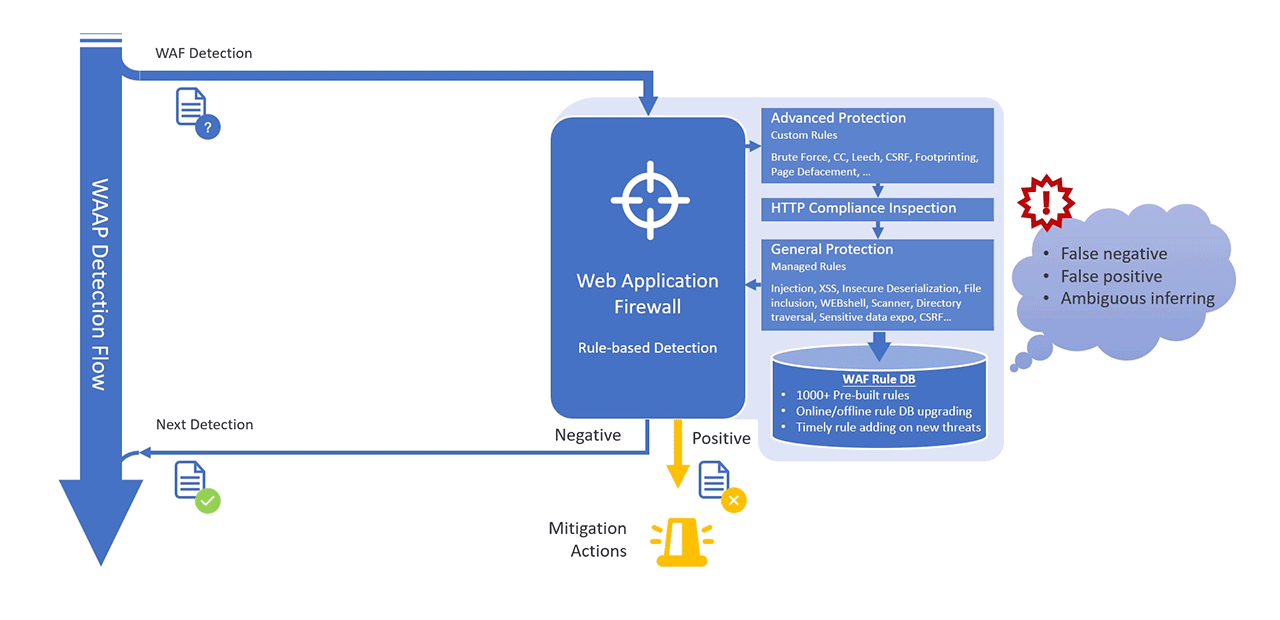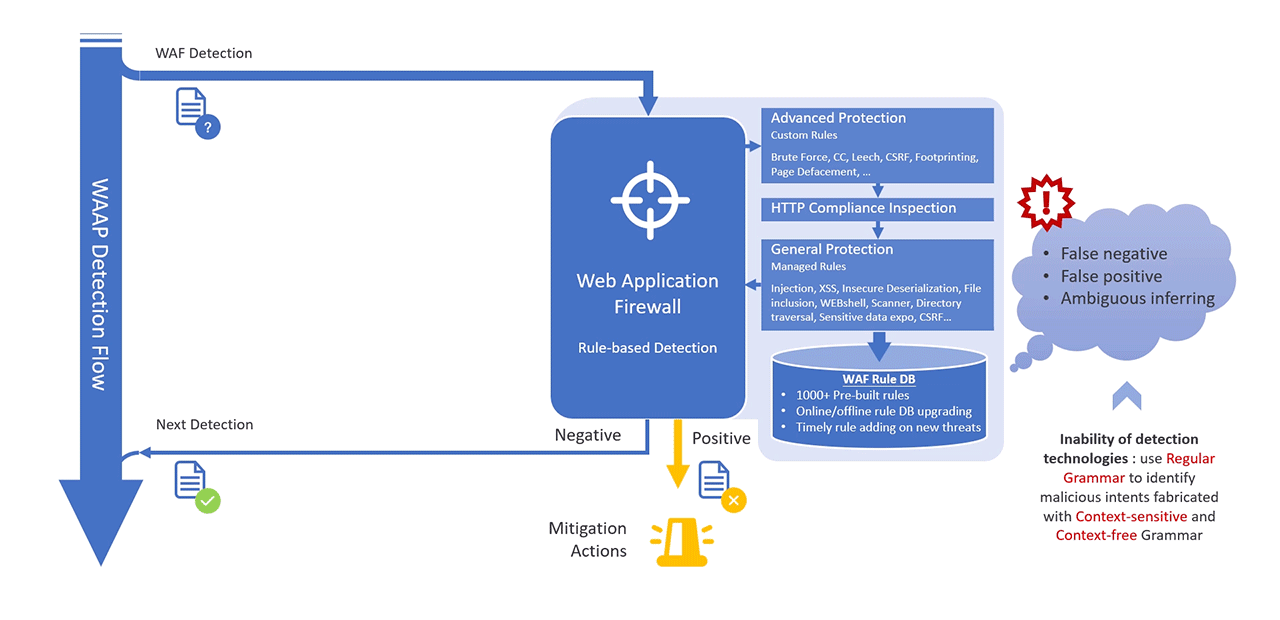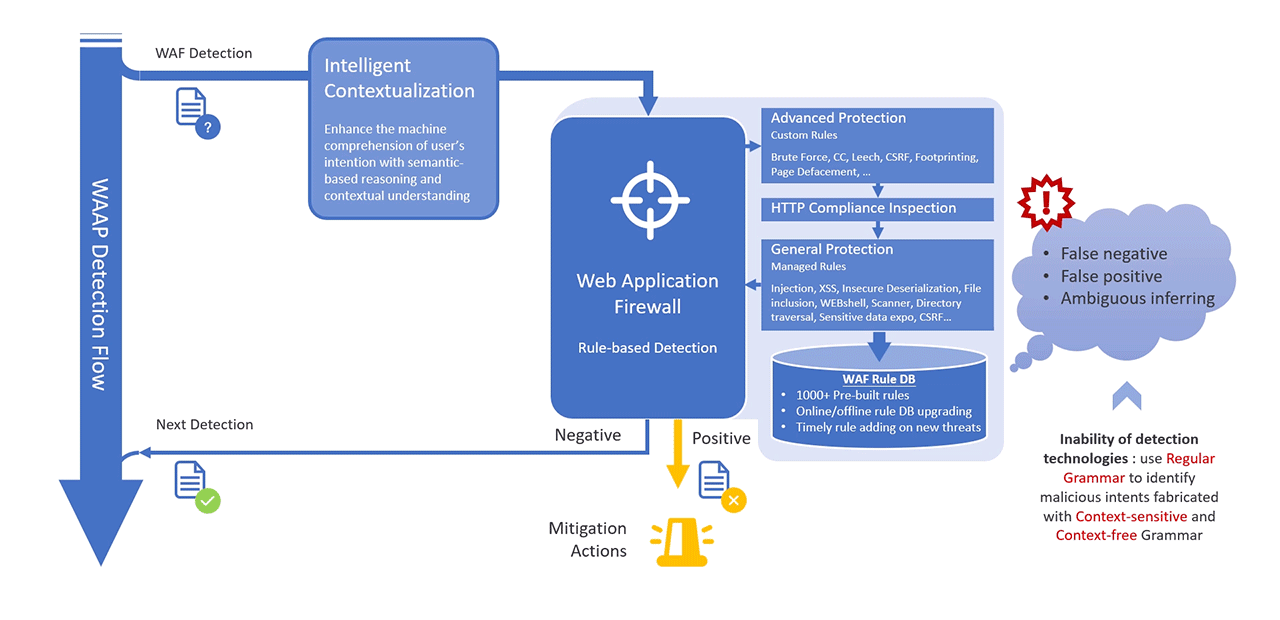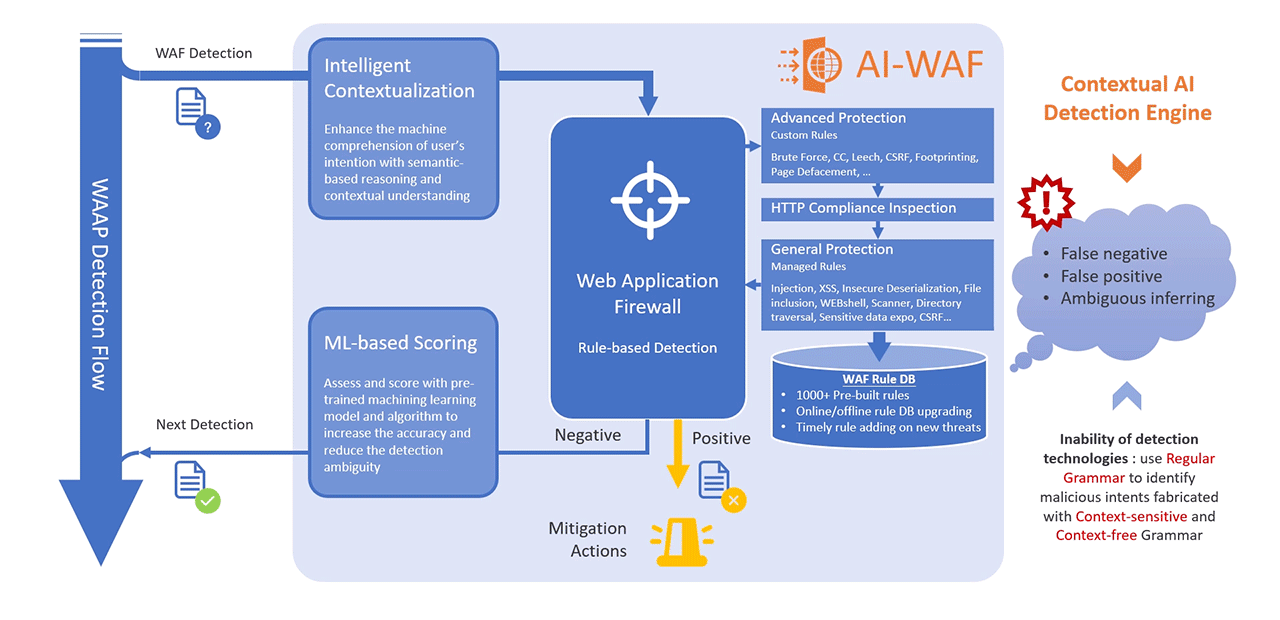
- ML-Based Scoring
- Applies machine learning models trained on extensive datasets to assess threat severity and likelihood.
- Continuously refines scoring algorithms based on emerging attack vectors and new threat signatures.
- Reduces false negatives by detecting anomalous patterns that deviate from normal traffic behaviour, even without predefined rules.
MaxiSafe's AI-WAF operates as a contextual AI-detection engine, embedding semantic analysis and multi-dimensional traffic correlation into its core. It processes complete request sequences, analysing headers, parameters, payload structures, and behavioural patterns to detect anomalies that evade pattern-based detection. This enables real-time identification of obfuscated, fragmented, or zero-day threats, forming a critical layer in the AI-WAF's adaptive inspection pipeline.
Contextual AI-Detection
In the evolving landscape of cybersecurity, the race between defenders and attackers accelerates. The interval between the first exploitation attempt and the first defensive patch is shrinking.
For example, Cloudflare observed a zero-day vulnerability being exploited just 22 minutes after its Proof-of-Concept (PoC) was published. In contrast, the most responsive rule update took 4 hours, leaving a significant exposure window.
To bridge this gap, MaxiSafe employs Contextual AI-Detection, which leverages contextual analysis to identify potential threats even before rule updates are deployed.
Benefits of Contextual AI-Detection
- Identifies context-specific attack patterns that evade conventional rule-based detection.
- Detects obfuscated payloads through semantic analysis, reducing false positives.
- Provides broader coverage against unknown threats by correlating multiple request attributes.
Why Contextual AI-Detection?
- Reduces false positives by correlating request elements to evaluate intent rather than isolated patterns.
- Adapts to new attack tactics through semantic analysis, mitigating 0-day exploits without requiring immediate rule updates.
- Provides broader detection coverage against evasive threats, including obfuscated payloads and encoded injections.
Examples of Contextual AI-Detection
-
SQL Injection Context Analysis
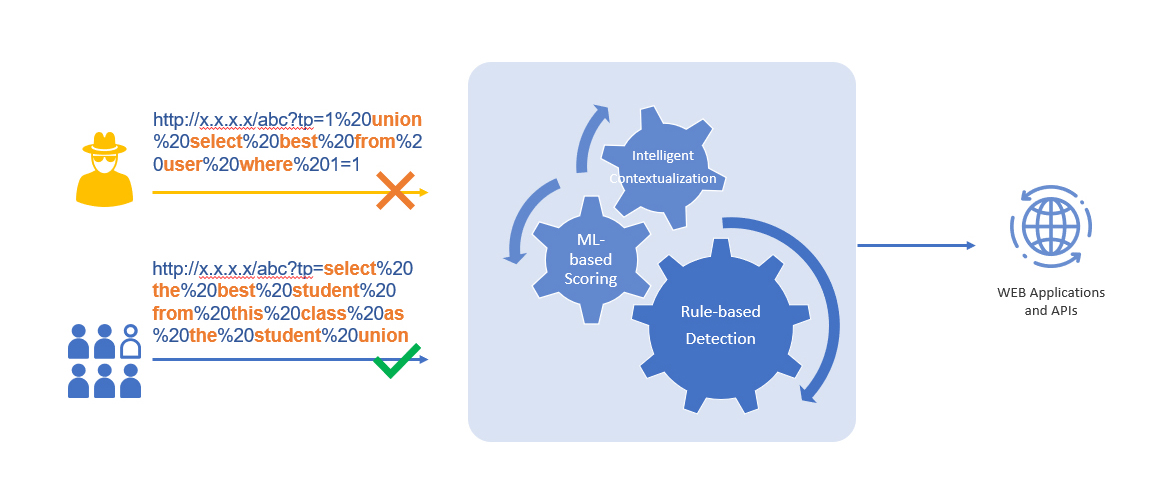
- Attack Payload:
http://x.x.x.x/abc?tp=1%20union%20select%20best%20from%20user%20where%201=1 - Legitimate Request:
http://x.x.x.x/abc?tp=select%20the%20best%20student%20from%20this%20class%20as%20the%20student%20union - Analysis:
- Rule-Based Detection identifies common SQL keywords but fails to distinguish intent.
- Intelligent Contextualization evaluates semantic structure to differentiate between malicious and legitimate queries.
- ML-Based Scoring assigns risk scores based on historical behaviour and known attack patterns, ensuring accurate detection.
- Regular requests are allowed to pass through to web applications and APIs, while malicious requests are blocked.
- Attack Payload:
-
Injection Attack Detection Analysis
Contextual AI-Detection applies semantic analysis to evaluate the actual meaning and intent of the request, reducing false positives in injection attack scenarios.
Input Rule-Based Detection Contextual AI-Detection <script>abc</script> Positive Allowed Non-malicious JavaScript tag <script>alert(1)</script> Positive Positive Malicious JavaScript function <script>a alert(1)</script> Positive Allowed Non-malicious JavaScript tag flagged as benign <a onclick="alert('onclick alert');">onclick</a> Positive Positive Malicious JavaScript function <a onclick=" a alert('onclick alert');">onclick</a> Positive Allowed Non-malicious JavaScript function flagged as benign Conclusion:
- Rule-Based Detection: Focuses on individual patterns, leading to multiple false positives.
- Contextual AI-Detection: Evaluates context and semantic structure to accurately distinguish malicious payloads from legitimate ones, effectively reducing false positives.
-
Obfuscated JavaScript XSS Payloads
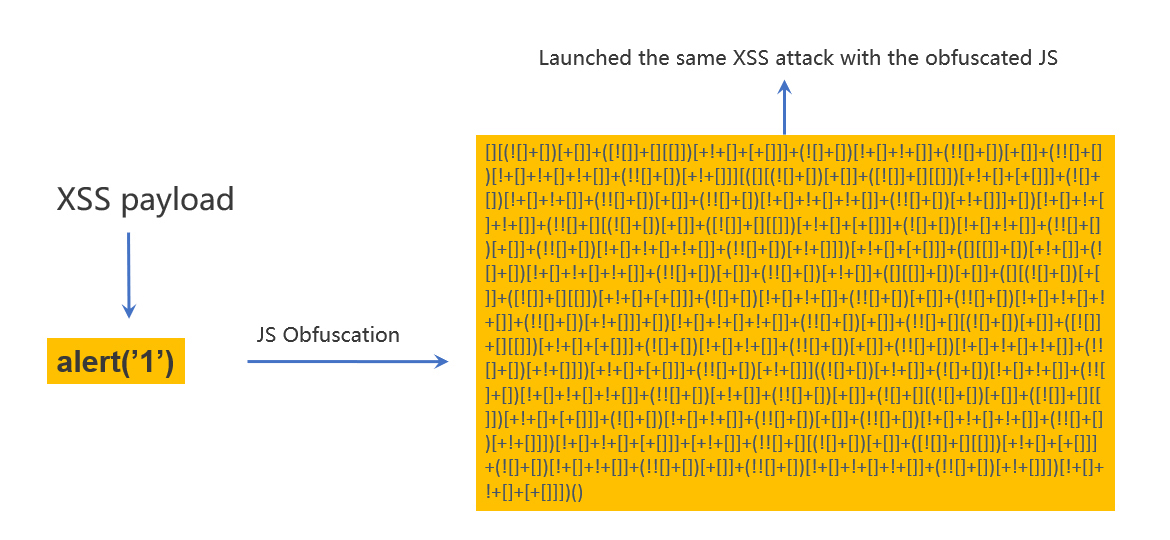
- Obfuscated Attack Payload:
[][(![]+[])[+[]]+ ... +[]]])() - Detection Process:
- Rule-Based Detection: Focuses on detecting specific patterns or keywords like
alert(). - Contextual AI Detection: analyses the logic flow and semantic structure to identify obfuscation and recognize underlying malicious intent.
- Semantic Analysis: Deconstructs the obfuscated payload to extract the core command and compare it against known attack patterns.
- Rule-Based Detection: Focuses on detecting specific patterns or keywords like
- Analysis:
- Contextual AI-Detection analyses JavaScript execution flow to detect malicious intent despite obfuscation.
- ML-Based Scoring correlates behaviour patterns to previous XSS attack signatures, minimizing false positives.
- Obfuscated Attack Payload:
Core Advantages of AI-WAF
AI-WAF consolidates traditional rule-based detection, semantic analysis, AI-driven threat scoring, and advanced enhancements to form a comprehensive security framework. It delivers broader and more accurate prevention by leveraging a contextual AI engine to detect sophisticated threats and reduce false positives. Additionally, AI-WAF provides higher adaptability by combining semantic analysis and machine learning algorithms with rule-based detection, minimising reliance on manual tuning and improving responsiveness to evolving threat landscapes.
- Traditional Rule-Based AI-WAF: Detects common vulnerabilities, such as injections, cross-site scripting, and CSRF, using predefined rules.
- Semantic Analysis: Analyses request context to identify hidden threats, such as command injection cloaked in legitimate requests.
- AI Detection: Employs machine learning to recognise evolving attack patterns and mitigate unknown threats before they escalate.
- Advanced Enhancements: Adapts to advanced threat vectors, including 0-day exploits, through continuous model updates and contextual learning.